Ok, I’m coming clean. Controlling access to our various servers has been a mess. Sure, we’ve stored passwords in a safe way (1Password for teams ftw!) but what happens if someone leaves the company or that root password somehow were to get out… Well, we did not have a plan for such a thing.
Sure, setting up ssh keys is easy, but we never got around to it. We manage more than a handful servers, and making sure the authorized_keys on these boxes is up to date just felt unmanageable.
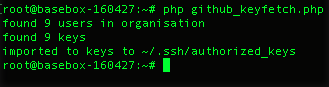
This changed today when i got the idea to make use of this GitHub’s feature which exposes the public keys. I wrote a little script that fetches all users within our GitHub organization, pulls down the public keys and updates the ~.ssh/authorized_keys-file nightly with a cron job.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| <?php | |
| # import github keys | |
| $ch = curl_init('https://api.github.com/orgs/EarthPeople/members'); | |
| curl_setopt($ch, CURLOPT_USERPWD, "XXX:XXX"); | |
| curl_setopt($ch, CURLOPT_TIMEOUT, 30); | |
| curl_setopt($ch, CURLOPT_RETURNTRANSFER, TRUE); | |
| curl_setopt($ch, CURLOPT_USERAGENT,'EpBot'); | |
| $users = @json_decode(curl_exec($ch)); | |
| curl_close($ch); | |
| echo "found ".count($users)." users in organisation\n"; | |
| if($users){ | |
| foreach($users as $user => $params){ | |
| echo "user: ".$params->login."\n"; | |
| $keys[] = file_get_contents('https://github.com/'.$params->login.'.keys'); | |
| } | |
| } | |
| echo "found ".count($keys)." keys\n"; | |
| if(count($users) === count($keys)){ | |
| file_put_contents('/root/.ssh/authorized_keys', implode($keys, "\n")); | |
| echo "imported to keys to ~/.ssh/authorized_keys\n"; | |
| }else{ | |
| echo "error, could not fetch keys for all users\n"; | |
| } |
Yes, this is PHP but when all you’ve got is a hammer – everything looks like a nail. This needs some error handling too, but I thought I’d share it anyway.
/Peder

